A world without the internet hardly seems imaginable. Let’s consider the fact that there are 4.66 billion active internet users worldwide, according to Statista. What used to take months to deliver takes no longer than a few seconds. Today, communication tools and how we exchange personal data and information have bridged the gap between therapists and their clients. Moreover, internet communication ensures an instant connection between people who aren’t in the same proximity.
Research demonstrates that the internet is a fantastic resource for the medical field with an abundance of advantages! With that being said, internet security should always be top of mind for any therapist looking to purchase a virtual care solution. But how do you know what to look for?
In our latest webinar, we sat down with the profound Lawrence Murphy, Psychologist & founder of Worldwide Therapy Online, established in 1994 as the world’s first online clinical practice to speak on Video Counselling: Security, Ethics, and Clinical decisions. In this blog, we highlight the 4 discussed essential security measures you should be looking for in your virtual care solution to ensure your practice and patient data are safe and secure.
1. Encrypted Messages & Communication: Why Should You Care?
With the evolution of virtual care, therapists and clients can quickly exchange messages, photos, videos, voice messages, documents, and other essential health data, improving the health care experience. However, serious privacy and security risks could undermine this experience if you’re not using a solution supported by encryption. What does encryption mean, and why should therapists care? Encryption itself is straightforward: It turns data into something that cannot be read when transferred from one device to another. With end-to-end encryption, the only people who can access the data are the sender and the intended recipients – no one else in between.
Here’s how encryption works when sending a message or sharing an encrypted file:
- A readable message (“I’d like to book an appointment today”) is encrypted into a scrambled message with the intent to be incomprehensible to anyone looking at it (“056393462050”).
- The encrypted message is sent over the internet, where others see the scrambled message (“056393462050”).
- When it arrives at its destination, the intended recipient, and only the intended recipient, will see. The decryption step uses the same secret key to convert the ciphertext back into the original data (“I’d like to book an appointment today”).
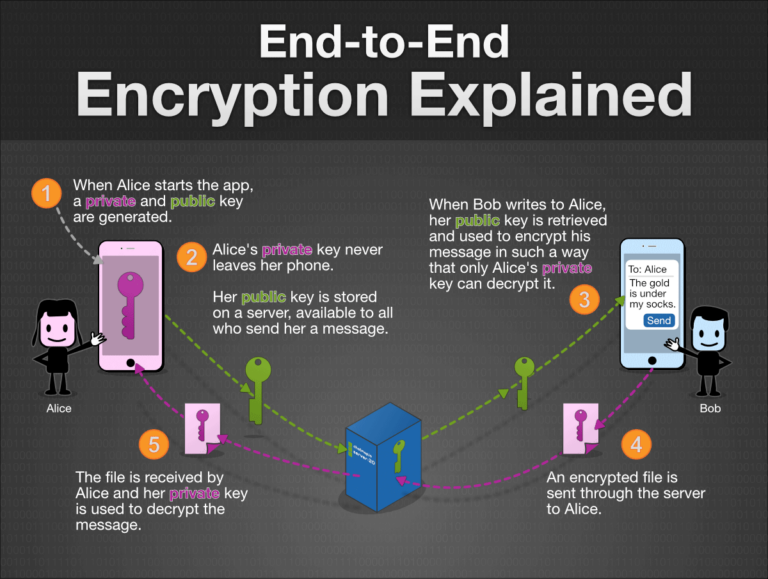
Source: chatmap.io
A trusted virtual care solution should always offer industry-standard AES 265 Bit-Encryption. The 256 indicates the number of possible key combinations. The higher the number of bits of encryption, the greater the number of possible keys, so the more difficult it is to compromise the encryption.
What happens when a therapist sends an email from an encrypted platform to a client who doesn’t have encryption?
While your email service provider might encrypt the email as you press send, if the data on their data server is not encrypted, it can be stolen or misused.
Let’s look at Google as an example. When emails are sent between different mail providers, both providers need to support TLS for the email to be encrypted in transit. If you use Gmail and your client or colleague uses an email provider that doesn’t offer TLS encryption, emails exchanged will not be unencrypted. This enables Google to scan the information in a TLS-encrypted email and expose that information to third parties.
Services like Gmail, Yahoo or Microsoft enable the provider to access users’ data on its servers because these providers hold copies to the decryption keys. As such, these providers can read users’ emails and files. In Google’s case, its possession of decryption keys has enabled them in the past to provide the Google account holder with targeted ads.
2.End-to-End Encryption Database
Let’s begin by defining a database. In simple terms, a database is an organized collection of structured information, or data, stored electronically in a computer system and can be expanded, updated, or retrieved rapidly.
According to the Institute of Medicine (US) Committee on Regional Health Data Networks, the term database embraces many different concepts, including paper records maintained by a single practitioner, vast computerized collections of insurance claims for Medicare beneficiaries, files of computerized patient encounter forms, cancer and trauma registries maintained by health institutions and researchers, and the major national health survey data of federal agencies.
EHR’s, EMR’s, and other virtual care platforms are examples of healthcare databases. They offer the ability to store, collect, manage, distribute and access patient health information electronically, improving patient care management. However, those features that make digital healthcare desirable—accessibility, transferability, and portability of patient health information—also present privacy and security risks.
Healthcare is the only industry where more breaches happen because of insider threats than outside malicious agents, and it’s tied for first place for the most breaches across all sectors.
–2018 Data Breach Investigations Report, 11th edition (Verizon)
Amidst the COVID-19 pandemic, therapists have been forced to transition from seeing their clients in-person to online. However, many therapists haven’t been trained in protecting security and patient privacy in an online setting. From 2010 to 2015, it was found that laptops (20.2%), network servers (12.1%), desktop computers (13%), and other portable electronic devices (5.6%) made up 51% of data sources of all healthcare data breaches and affected more than 500 individuals.
To ensure client privacy and confidentiality, therapists should contact their virtual care platform and ask about AES 265 Bit-Encryption at every endpoint.
3. Safeguarding Privacy: Healthcare Compliance Regulations
Let’s begin by defining a database. In simple terms, a database is an organized collection of structured information, or data, stored electronically in a computer system and can be expanded, updated, or retrieved rapidly.
Healthcare organizations and therapists that handle confidential and sensitive information must adhere to jurisdiction privacy laws, organizational policies, and ethical standards set forth by the Health Insurance Portability and Availability Act (HIPAA), the Personal Health Information Protection Act (PHIPA), the Personal Information Protection and Electronic Documents Act (PIPEDA), the Personal Information Protection Act (PIPA) or other applicable personal health information legislation where it operates.
If your virtual care solution fails to safeguard sensitive data (including confidential medical records) appropriately, healthcare providers could face a violation or lawsuit. Always ask your service provider if they are compliant with your state or province’s privacy and security laws.
For further information on a few jurisdiction’s set of privacy & security rules & regulations, you can refer to the following governing resources:
4. Where is the server located, and why does it matter?
Let’s begin by defining a database. In simple terms, a database is an organized collection of structured information, or data, stored electronically in a computer system and can be expanded, updated, or retrieved rapidly.
If your practice handles any medical or health records, you must have a robust healthcare data management plan in place. For most healthcare facilities, this means digitizing patient health records and storing (and backing them up) on a secure server. The specific regulations governing access to data from servers depend on the jurisdiction in which servers are located. In Canada, federal (Personal Information Protection and Electronic Documents Act) and provincial (Act respecting the protection of personal information in the private sector) laws govern data retention in servers and server operation by digital health tools manufacturers.
What would happen if a therapist residing in Canada uses a virtual care solution with a server in the United States?
Any data transferred from a device or software to servers located in a foreign country might expose the user to additional risk.
For example, following September 11, 2001, in New York, the Patriot Act was passed in the United States. It allows several American public entities to access data hosted on servers located on its territory without the user’s authorization. The problem is that many Canadians use American services. Thus, they expose themselves to some form of surveillance by the American authorities without being aware of it, even if they aren’t citizens of the United States (learn more about the Patriot Act here).
Not sure where your server is located? Ask your service provider, and as a rule of thumb, if you’re in Canada, it’s a wise decision to pick a virtual care solution with Canadian servers.
A Secure and Reliable Virtual Care Solution You Can Trust
At Adracare, we understand just how important it is to keep data secure. Any communications and personal information are encrypted in transit, in the database, and at rest, leveraging industry-standard AES 256-bit encryption and in compliance with HIPAA, PHIPA, PIPA and PIPEDA.
The Adracare Platform maintains strict geographic boundaries, and as such, data for patients and providers in one country never crosses into another. Adracare deploys its solution in data centers in Canada, the United States of America, the United Kingdom, Australia, Netherlands, and new data centers are constantly added to meet each region’s personal health information regulations.
Are you interested in seeing how our all-in-one virtual care solution can protect your security privacy and security? Set up a free trial for one month or contact us today to speak to one of our experts.





